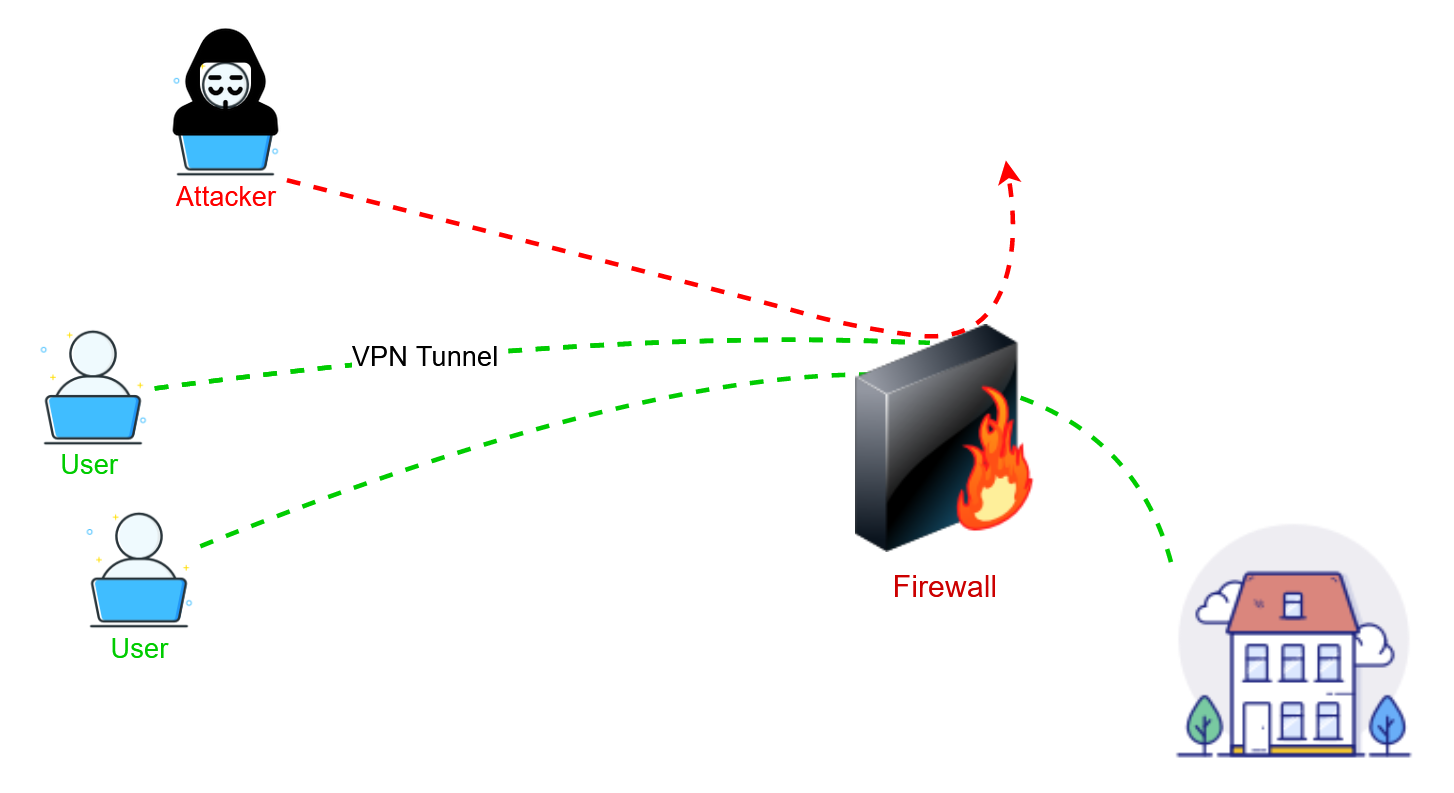
Advanced Firewall protection solutions configured by an award-winning team with Information Security Expert certifications. So that your organization doesn’t incur money loss and reputational damage as a result of cyberattacks.
With the evolution of technology, information security has become a real challenge for companies. As specialists develop advanced solutions for securing and encrypting communication channels, new ways of avoiding protections are constantly emerging.
Using the technology offered by Firewall, you can protect your company from cyberattacks and prevent security breaches that leave open doors to IT networks for hackers. Imagine what could happen if cybercriminals managed to access your data.