We test the cybersecurity vulnerabilities of all digital assets in your company. We offer you the necessary support to be able to face even the strongest hacker attacks.
In any industry, unauthorized access to company resources and customer data is a major issue that cannot be ignored. Especially in compliance-based industries such as finance, healthcare and legal services, you can never be too careful about digital assets and confidential information.
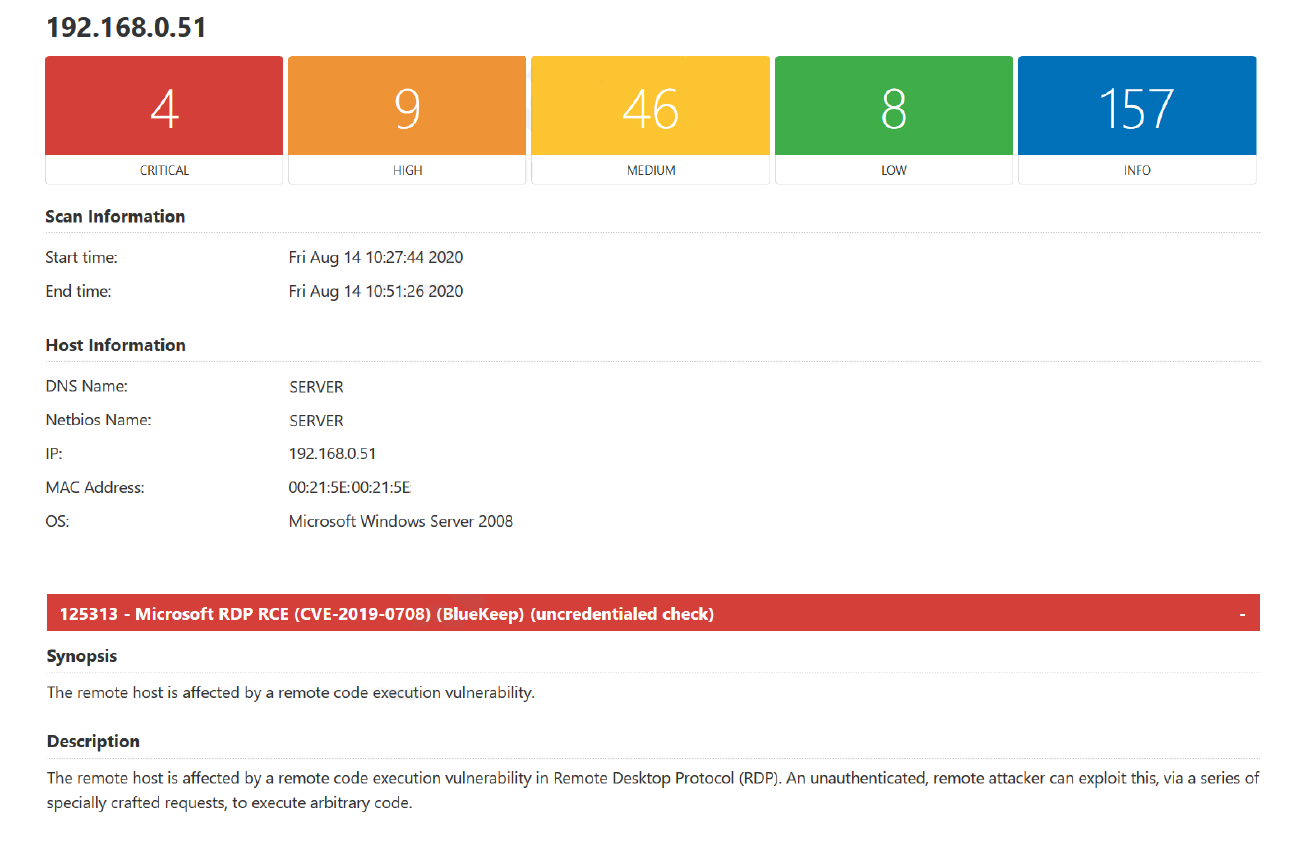
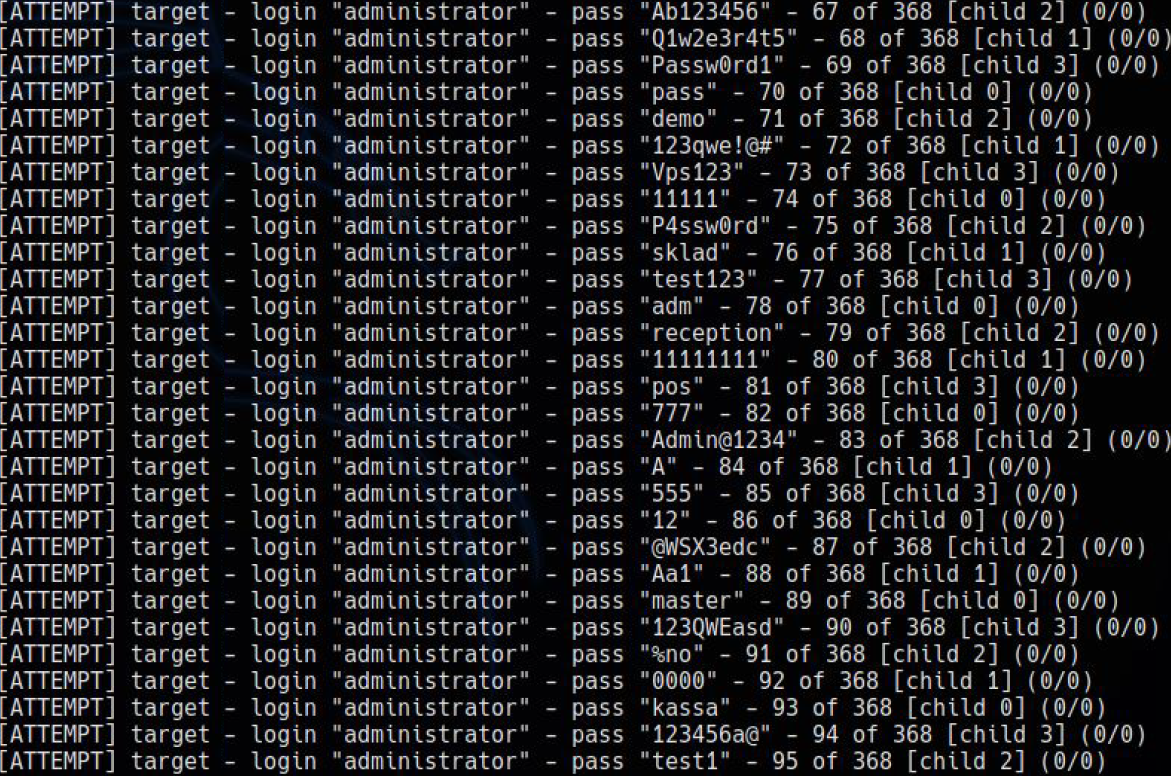
The best way to eliminate IT security vulnerabilities in your company is to think like the cybercriminals who would exploit them. And this can only be done properly by certified cybersecurity experts, through penetration testing, also called pen test or ethical hacking.
The Magnetic IT Services team includes engineers with prestigious certifications in cybersecurity. They will simulate the fact that your network, servers, applications, devices, business operations, and your team are victims of cyber threats similar to those in the real world. They will be able to tell you how to protect yourself.
How vulnerable is your company to a cyberattack ?
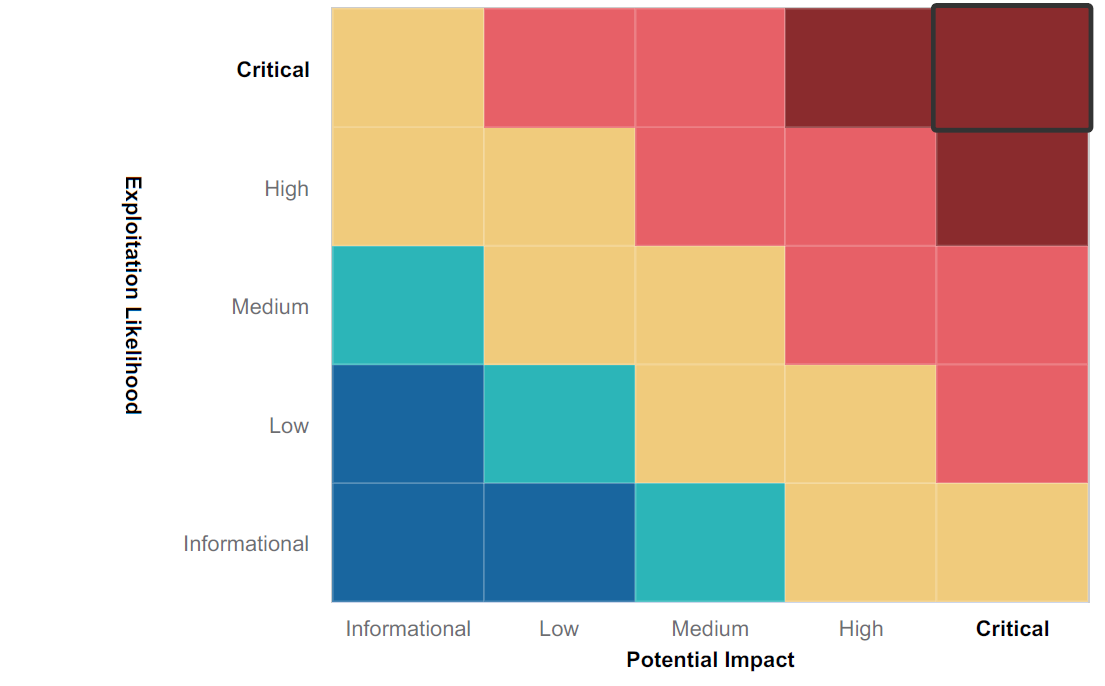
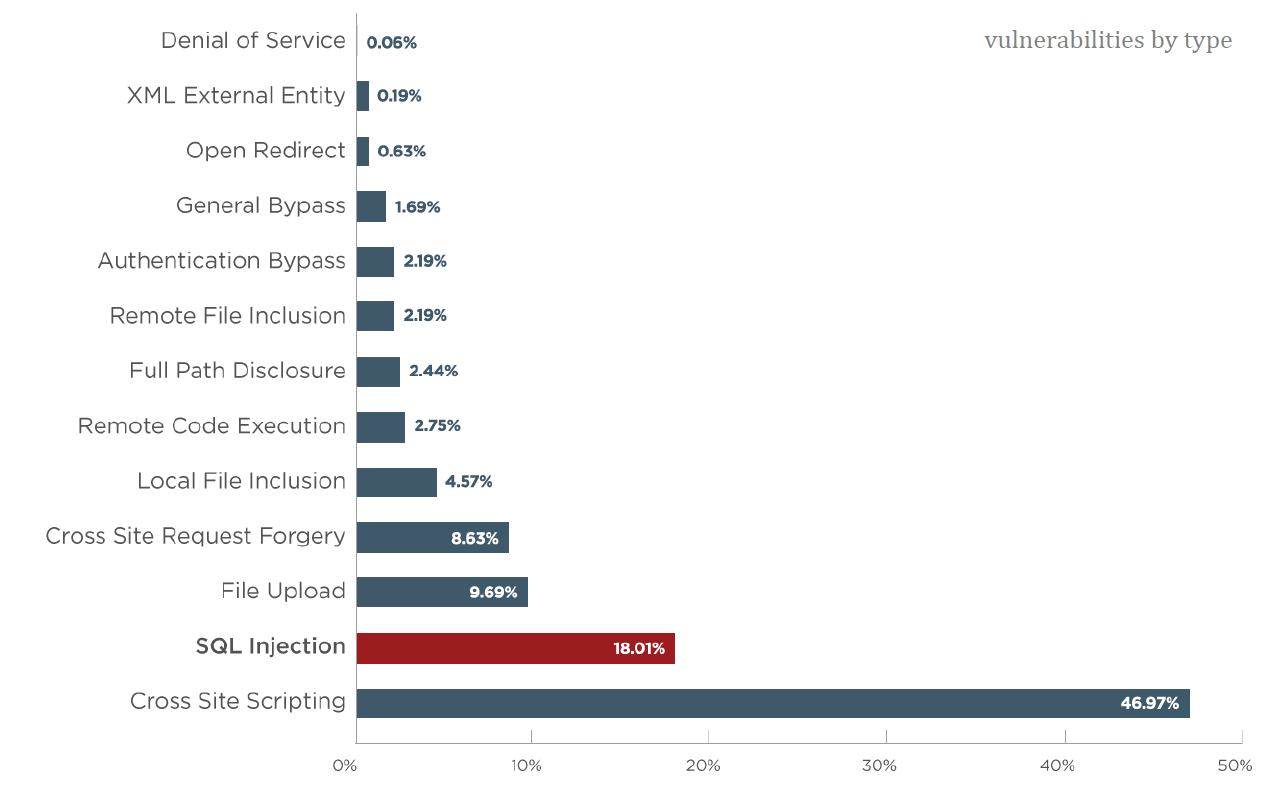
The main objective of a pen testing (penetration testing) is to identify vulnerabilities in your organization’s security strategy. From experience, we know that, although a security policy may focus on preventing and detecting an attack on systems, it may not include a strategy to limit the damage caused by a hacker. The test reveals the weaknesses of the company security policies.